EAT CAM RECORDER
Webcam Recorder records webcams to AVI, FLV, WMV files and watch them whenever you want. Work with MSN, Skype, ICQ, AIM, and Yahoo! Messenger. Audio can be recorded from any source. With Webcam Recorder you can replay some of your favorite moments. Webcam Recorder can record anything which can be displayed on your screen - webcams, streaming video, video chat and instant messaging software. Webcam Recorder is the easiest and fastest way to record webcam of your chat partner to the hard disk for replay in future.
Key Features
- Work with MSN, Skype, ICQ, AIM, and Yahoo! Messenger that supports the Webcam feature.
- Export of recorded streams to AVI, WMV (Windows Media Video) and FLV (Flash Video) format.
- Record both audio and video streams.
- Audio can be recorded from any source, including microphone, line-in, or speakers.
- Real time compress the webcam streams so to make the output media files smaller and not occupy too much disk space.
- Easy to record and playback
System requirements
|
Eatcam Webcam Recorder requires the system to be configured with the following equipments as a minimum:
|
HOSTS MAN
Features
Screenshot
Features
- Built-in host file updater
- Enable.Disable hosts file
- Built-in host editor
- Scan hosts 4 errors, duplicates and possible hijacks
- Host file backup manager
- Exclusion list
- ...
Download (Installer version)


- Version: 4.2.97
- Released: September 27, 2013
- Size: 2.67 MB
- Requirements: Windows XP SP2, Server 2003 SP1, Vista, Server 2008, 7, 8, Server 2012
- License: Freeware
- Download: [Mirror 1], [Mirror 2]
Download (Zip vers

ion)
- Version: 4.2.97
- Released: September 27, 2013
- Size: 3.08 MB
- Requirements: Windows XP SP2, Server 2003 SP1, Vista, Server 2008, 7, 8, Server 2012
- License: Freeware
- Download: [Mirror 1]

GET RIGHT DOWNLOAD MANAGER
GetRight® Screens.
A picture is worth a thousand words. These show the basics about how GetRight loks and works. Normally, GetRght just is running down with your tray icons, waiting to take over any downloads when you click on them i your web browser.
The top icon ere is GetRight's. The lower one shows the older style GetRight icon, for anyone with an older version of GtRight.
Save o Open
| When yo do click a file in your browser that GetRigh should download for you, it first pops u a question asking if you want to Open the fil (so it will be automatically saved on yourcomputer and opened when done) or to Sav the file (you can choose where it is saved, an can open it when you wish.) Jst like many other prompts in GetRight, this indow shows a simple checkbox if you wantto skip and not see it again | 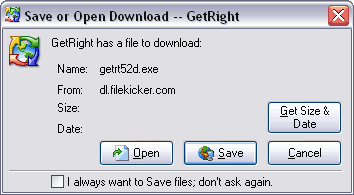
|
Save A
| If you chose "Save" on the window hown above, it will show a
SaveAs window so you can contro where the file is saved on your omputer, the name, etc.
If yu choose "Open" in the widow above, it will skip
this and g directly to the Downloadin window shown below
You can see a few ofthe extra choices on the bottm half of the window, they giveyou quick access to set thins like where in the ordering to dd the file, to give a comment abut the file, etc. | 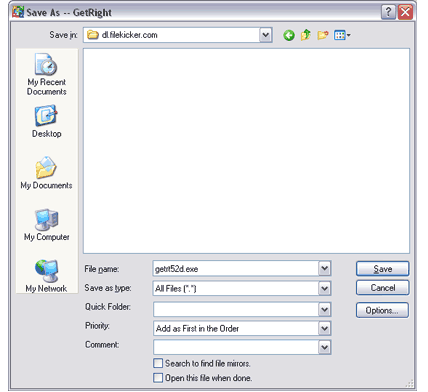
|
Downloding
| After pickin where to save the file, the Download window shws.
This window shows the status of the downlad such as how big the file is, how much GetRighthas downloaded,
how much time is left, etc
Yu can easily Pause and Resume the download ere--that Resume button swiches to be Pausewhen the download is in working
And using the Options buton (which shows a menu of choices) you can do thngs like set the file to be run when the download fnishes, show or hide the speed graph, pick to us a different skin, and more. | 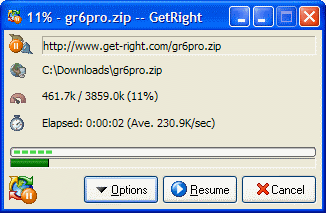
|
When you Dwnload is Finished
| If you clicked the Sve option on the "Save/Open" window above, when your ownload has finished, GetRight will show a simple tip window Clicking the text or image will let you easily run the file. (If yo clicked Open on the "Save/Open" window, the file will run hen it finishes downloading.) You can click he little buttons to open the folder where the file was downloaed and more. Right click the window (when it pops up on our computer, not this sample image!) and you can choose ho it will be shown--disappear after a few seconds, or say until ou close it; solid or semi-transparent; etc. | 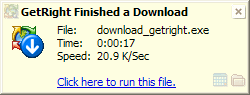
|
Dowload Status
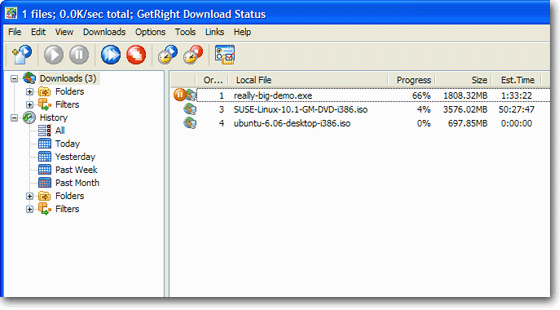
ConfigurationThe Configuration window is another place where you ca control many things about how GetRight works. There is a lo here and it can be a bit overwhelming, but you don't have o change anything for GetRight to work--these just give you coices.
If you want to cange something about how GetRight works, you can, and this is the place to do it. You can get to the confiuration window by Right clicking the tray icon, then the "GetRight Configuration".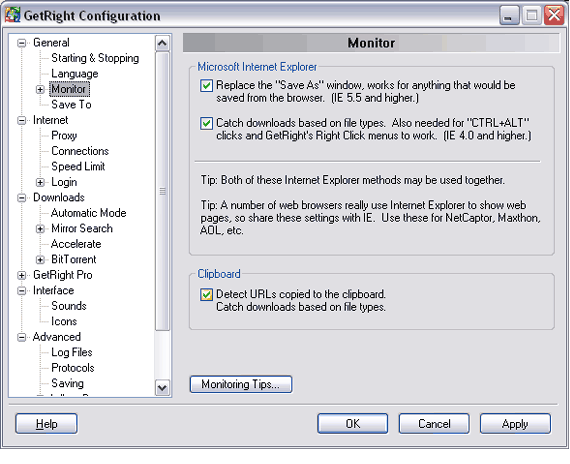

SILENT SCREEN
Computer usage among teenagers is so comon in today’s society but misuse of it could lead to very bad consequence. While parents may not ableto keep close eyes on them whole day and night and hence the need of good monitoring system is neede to ensure the proper usage. For web browsing, parents may still able to check through browsing history o find out which websites their children had browsed during certain period but in case there is a need to track the computer usage even inclusive offline activities such as reading documents, playing games and etc, the this application software will be able to help you. Named as Silent Screen, it monitors all computer usag with screens captured in predefined internal while the application software is running in background scretly.

Silent Screen is easy to setup and se. Once after launched, users will be prompted to select specific folder on where to store all the captured imges. Besides, it featured a hot key combination that allows parents to hide the small program icon in taskbar making it totally invisible to PC users. To make it more secure without being able to be turned off by yur smart kids, parents can even set password to protect the settings. On top of this, parents can set specificintervals of how fast each snapshot will take place throughout the monitoring process. By default, it will be et to 2000ms (or 2 seconds) but can be changed to suit own preference depending on how many scren captured is needed without overflowing the memory usage. Take note that you will need to ensure suffcient memory space if you intend to lower the interval values since there will be much more image files (in PG format) being captured and stored in your local hard disk space.
The application software s free for 30 minutes usage per session. In case you need longer time than that, users can upgrade to unlmited usage at $6 only. If you think it suits your need, just go and download one for trial at RapidSoftware

REAL IP HIDE
Key Features
- Hide Your Real IP Address
Be assigned fake IP addreses from different countries to conceal your real IP. - Anonymous Web Surfing
Surf anonymously withfake IP, whenever you want to. - Protect Your Identit Against Hackers
Protect you from hakers and identity thieves who will be tricked by your fake IP - n-ban Yourself from Forums or Restricted WebsitesReal Hide IP allows you to access any forums, blogs or websites that have ever banned you
- Prevent Websites from Tracking Your Online Ativities
Hide your real IP when you are surfing the Internet o prevent you from being tracked by websites.


DRIVE LOCKER

ACTUAL SPY
A useful key logger
 Many users think of spywae as a serious danger. This is not surprising
because hackers often use key loggers” to log all keystrokes of a user.
Their aim is to interceptpasswords, keywords and other important
information. However, spware can be very helpful sometimes. And there are
examples and exaples. For instance, a system administrator can install a
spy on the localnetwork server and he will always know if the computer
was used or not nd what operations were performed.
Many users think of spywae as a serious danger. This is not surprising
because hackers often use key loggers” to log all keystrokes of a user.
Their aim is to interceptpasswords, keywords and other important
information. However, spware can be very helpful sometimes. And there are
examples and exaples. For instance, a system administrator can install a
spy on the localnetwork server and he will always know if the computer
was used or not nd what operations were performed.Of course, spyware has a wider range of purpose. Parents can use it secretly to see what children do with the computerwhen the parents are away. School teachers can use spyware to cntrol their students’ activities. But it is especially useful when it is a pat of the information security system on your computer. Yes, exactly, utilities usually used by hackers can help ou resist them. To do it, the owner of the computer or its constant user should install this utility. After that,he or she will know who uses the computer and for what purpose
However, it should be mentiond that it is not all spyware that can be
used as a security tool. Such program must have a set of features tht
most key loggers lack. Let’s take Actual Spy developed by the Actual Spy
Software company for examle. This key logger was developed as an aid to
computer owners and their constant users

To start with, lt’s name the main features of Actual Spy. The first one
is “Keyboard”. As you can judge from its name, thismodule is responsible
for logging all keystrokes. The utility also logs the case of each
character and can easiy log almost all key combinations.
Another pleasant thing is that Actual Spy dos not log all keystrokes together, but groups them according to their programs. In other words, log files show the title of the window the text was typed in. At the same time, a lot of key loggers lack this feature and thePC owner cannot use the log files to tell what program was used to type the text. However, this information s very important because some keystrokes are quite acceptable in one program, but can be harmful in anoter. But that is not all. Another useful feature in Actual Spy is the “Show only characters” option. You can nable it using the corresponding checkbox in the log view window. After that, only the typed characters are hown instead of all pressed keys. It means actually that the user will see only the text typed while he or shewas away. This feature allows you to make backup copies of your texts with Actual Spy. Suppose you ae working in some program and it is suddenly closed because of a failure. The typed text will be saved in he log files of our spy.
The next feature in Actual Spy is “Screenshots”. The proram takes screenshots at the intervals the user specifies (by default – every 5 minutes). Now PC owner wil see with his or her own eyes what the computer is used for while he or she is away. You can customize ths option of course: specify the maximum space screenshots can take, their quality, hide the cursor from the creenshot, etc.
We move on to the next tab of the main window labeled “Programs”. I shows the list of software started and closed while Actual Spy was working. And actually they are not progrms, but windows.
Another pleasant thing is that Actual Spy dos not log all keystrokes together, but groups them according to their programs. In other words, log files show the title of the window the text was typed in. At the same time, a lot of key loggers lack this feature and thePC owner cannot use the log files to tell what program was used to type the text. However, this information s very important because some keystrokes are quite acceptable in one program, but can be harmful in anoter. But that is not all. Another useful feature in Actual Spy is the “Show only characters” option. You can nable it using the corresponding checkbox in the log view window. After that, only the typed characters are hown instead of all pressed keys. It means actually that the user will see only the text typed while he or shewas away. This feature allows you to make backup copies of your texts with Actual Spy. Suppose you ae working in some program and it is suddenly closed because of a failure. The typed text will be saved in he log files of our spy.
The next feature in Actual Spy is “Screenshots”. The proram takes screenshots at the intervals the user specifies (by default – every 5 minutes). Now PC owner wil see with his or her own eyes what the computer is used for while he or she is away. You can customize ths option of course: specify the maximum space screenshots can take, their quality, hide the cursor from the creenshot, etc.
We move on to the next tab of the main window labeled “Programs”. I shows the list of software started and closed while Actual Spy was working. And actually they are not progrms, but windows.
And, finally, here comes the last tab in Actual Spy labeled “Clipboard.
Everything is also quite obvious here. It shows everything that was copied
into the clipboard during the wrk of the spy. Most users will not find
this feature interesting, but it can be very useful sometimes. The
clpboard is often used to copy long and complicated passwords. So if you
see a keyword in the clipboard ist, you know that you should change it as
soon as possible

So, we have examined the main features of Actual Spy. Now let’s talk about
the special features of this spy. First, Actual Spy is an invisible
program.You will not see any signs of its presence in the system and
antivirus programs will not detect it. Moreover, in the program settings
you can select such options as “Remove the shortcut from the desktop”,
“Remove te program from the menu”, “Remove the program from the “Add or
Remove Programs” list” and “Hide theprogram folder”. If the PC owner
enables these options, nobody will even suspect that there is spyware on he computer.
Besides, it is really great that Actual Spy can proect its log files from unauthorized access. The PC owner can install a password that must be entered ever time Actual Spy is started. Besides, all data the program saves is automatically encrypted. Thus, it is hardl possible to read the log files without using the Actual Spy utility.
And he last part of our review will be devoted to reports. Actual Spy can generate reports based on its log files n two formats: text or HTML. The user can specify the necessary time interval and select necessary typs of log files. But there is more to it than that. Actual Spy can also create reports automatically and send thm to the specified e-mail address. Moreover, the reports can be generated either at the specified intervals or when the log file exceeds the specified size (both parameters are specified by the user). A lot of system administrators will appreciate this feature because they will be able to immediately respond to someone's work on the server.
So we can see that the advanced key logger Actual Spy can be an important part of the information security system. This utility will be really helpful to both the system administrators of local area networks and home users.
Besides, it is really great that Actual Spy can proect its log files from unauthorized access. The PC owner can install a password that must be entered ever time Actual Spy is started. Besides, all data the program saves is automatically encrypted. Thus, it is hardl possible to read the log files without using the Actual Spy utility.
And he last part of our review will be devoted to reports. Actual Spy can generate reports based on its log files n two formats: text or HTML. The user can specify the necessary time interval and select necessary typs of log files. But there is more to it than that. Actual Spy can also create reports automatically and send thm to the specified e-mail address. Moreover, the reports can be generated either at the specified intervals or when the log file exceeds the specified size (both parameters are specified by the user). A lot of system administrators will appreciate this feature because they will be able to immediately respond to someone's work on the server.
So we can see that the advanced key logger Actual Spy can be an important part of the information security system. This utility will be really helpful to both the system administrators of local area networks and home users.








No comments :
Post a Comment